Web Site Designing
Replace these every slider sentences with your featured post descriptions.Go to Blogger edit html and find these sentences.Now replace these with your own descriptions.
Mobile Application Designing and Developing
Replace these every slider sentences with your featured post descriptions.Go to Blogger edit html and find these sentences.Now replace these with your own descriptions.
E-Commerce Website Development
Replace these every slider sentences with your featured post descriptions.Go to Blogger edit html and find these sentences.Now replace these with your own descriptions.
Sunday, November 6, 2011
Sunday, October 30, 2011
VGA to RCA Cable_Connector
The length of this HDMI to VGA is 5ft and there will non be any problem in connecting through two devices. There is golden plate in the HDMI to VGA adapter and it make the high-speed data transfer. If you want to do a presentation on a big screen for hundreds of people then you will need special adapter to convert the video and audio from a small twist to a big screen and the HDMI to VGA is one of the best employed adapter which has ability to show more clear images with high resolution of video quality. Some connectors have the trouble of hardness and in that case it becomes very hard to wrap the cable but this HDMI to VGA adapter has got moderate softness that one can easy fold it while putt inside the bag or while adjusting the wire in a small space if there is extra while connecting.
You power have faced the problem of slow video or cutting video or even auto-pausing effects while transferring the video on a big screen through a connector because those are non that much efficient but ‘HDMI to VGA and 3 RCA Audio Video AV Adapter Cable‘ has extremely high working performance and there will non be any deceleration or cutting video or auto-pausing problems. This can be the best thing to entertain with the family members; you can use this HDMI to VGA connector in connecting the high-definition DVD player and the projector and finally enjoying the high quality display effect on a big screen with your family. The materials used in making this HDMI to VGA adapter is of high quality and so it is durable for long time, there will non be any problem at all during its usage time.
The design and coloration of HDMI to VGA and 3 RCA Audio Video AV Adapter Cable is amazing and this is why attraction is also an extra feature included in this cable. HDMI toVGA cable is portable and can be put inside your bag; you can take it out whenever its use is required. The reasonable price is another nice aspect of this HDMI to VGA cable. If you are provision on having this amazing fellow then it is guaranteed that you will get lots of features just spending little money. You will get money-back policy while ordering the product from Dinodirect.com, returning can be done if you are not slaked with the product.
Wednesday, October 26, 2011
Which type of woman...
Which type of woman do you like?
1. HARD-DISK Woman: She remembers everything you say and do, FOREVER.
2. WINDOWS Woman: Everyone knows that she can't do anything right, but you can't live without her.
3. EXCEL Woman: They say she can do a lot of things but you mostly use her for only your basic needs.
4. SCREENSAVER Woman: She is good for nothing functional, but at least she is exciting, colorful, and lots of fun.
5. INTERNET Woman: Difficult to access and hard to keep running.
6. SERVER Woman: Claims to be available to you, but Always busy when you need her.
7. MULTIMEDIA Woman: She has a way of making horrible things look very beautiful.
8. CD-ROM Woman: She always has you on the move, going faster and faster.
9. E-MAIL Woman: Out of Every ten things she says, eight are plain nonsense.
10. VIRUS Woman: Also known as “WIFE”; when you are least expecting her, she shows up, installs herself, and starts gobbling up all your resources. If you try to uninstall her, you will lose almost every thing. If you don't try to uninstall her, you will still have nothing.
Sunday, October 9, 2011
How to install android OS on PC
Recently, we’ve been hard at work improving Android Market to give you new ways to find great applications and games, purchase books, and rent movies. Today, we’re releasing a new version of Android Market which makes all of these available on phones (Android 2.2 and higher).
In the U.S., you’ll be able to rent thousands of movies, starting at $1.99, right from Android Market on your phone. With the Videos app, available in Android Market, there’s no more waiting for downloads, syncing, or worrying about storage space. Simply sign into Android Market with your Google account, and you can rent movies from anywhere – the web, or your Android phone or tablet – and start watching instantly. You can also download movies to your device so they’re available for viewing when you don’t have an internet connection.
Also in the U.S., you can now purchase books from Android Market on your phone. Like movie rentals, books are linked to your Google account, so they’re instantly available across all of your devices – computer, phone, or tablet – without the need for wires or downloads.
You’ll be delighted to find we’ve overhauled Android Market to make it faster, easier, and more fun to discover great apps, movies, and books. We’ve created more space to feature some of the most interesting content of the week on the home page. We’ve added more top charts, with newer, more relevant items, and we’ve made it easy to swipe through these charts as you browse the store. We’ve also introduced new collections of great content, like staff picks and Editors’ Choice apps.
The new Android Market will be rolling out in the coming weeks to Android 2.2 and higher phones around the world. You don’t need to do anything - the update is automatic on supported phones. If you’re in the U.S., you’ll also be able to download the Videos app, rent movies, and buy books once you receive the new Android Market.
Your phone is about to get a lot more interesting! Enjoy the new Android Market.
How to Install Android on Local Desktop Computer
First of all open this link and Download Android V 0.3 download here:
http://code.google.com/p/live-android/downloads/list as per Above Video.
Posted by Paul Montoy-Wilson, Product Manager
Sanket Barot
Tuesday, September 13, 2011
China renews operating license of Google
 China said that it has renewed Google's license to operate in the world's largest online market, after the US company last year moved its Chinese search engine overseas in protest over censorship.
China said that it has renewed Google's license to operate in the world's largest online market, after the US company last year moved its Chinese search engine overseas in protest over censorship.
The Ministry of Industry and Information Technology named Google's China website operator, Beijing Guxiang Information Technology Co. Ltd., as one of 137 firms whose licenses were renewed following adjustments in their operations.
The ministry had ordered the adjustments after some firms had changed shareholding structures without official permission, provided services beyond their approved business range or had lax information security controls.
The ministry, which posted the license renewals on its website, did not specify the kind of changes individual companies had to make.
Google spokeswoman for China Marsha Wang confirmed to AFP that the company had been granted the license renewal.
"We have passed the 2011 annual assessment (of the license)," she said.
This means Google's Internet content provider license in China has been extended for one more year, she said.
Google said in March last year it would no longer bow to government censors and effectively shut down its Chinese search engine, re-routing mainland users to its uncensored site in Hong Kong.
Google has maintained that such an approach complied with Chinese law.
Saturday, July 16, 2011
Protect your Data, Passwords
It’s hard to remember multiple passwords and keep sensitive information secure in this digital age. Whether you use a Mac, PC or smartphone, various free tools can help you with this by securing all passwords with a master password, encrypting data and securely wiping any sensitive info explain Karan Bajaj & Hitesh Raj Bhagat
EXCLUSIVELY FOR MAC OSX
Encrypt This
Simply drag and drop the files/folders you want to protect onto the application’s icon. It will then ask you to set a password for accessing the files and then create a protected disk image of your content.
Get it from www.nathansheldon.com
Pastor
One of the simplest password managers for MAC, Pastor requires a master password to be set to access all the stored passwords and serial numbers. It even comes with a password generator.
Get it from www.mehlau.net
Password Vault Lite
This app stores all your passwords online and safeguards them with a master password. It can also run from a USB drive and features an auto-lock timer that locks the program after some inactivity.
Get it from www.lavasoftware.com
TXTCrypt
As the name suggests, TXTcrypt works for text and not for files. Simply type in any text (mails/notes), protect it with a password and share it with anyone. The receiver needs the password and TXTcrypt to decrypt and read it.
Get it from www.txtcrypt.com
EXCLUSIVELY FOR WINDOWS PCs
AxCrypt
An open-source encryption solution, AxCrypt integrates with Windows Explorer to give you encryption options with a simple right click. The developers also offer portable versions (to use on flash drives).
Get it from www.axantum.com/axcrypt
Crypt4Free
Crypt4Free is a small package that allows easy encryption and schredding (secure deletion) of files on your Windows system. It also compresses encrypted files to reduce size while sending.
Get it from www.aeppro.com
MyPadlock
MyPadlock locks down all your passwords using 128-bit AES encryption — all you need to remember is one master password in order to access all the passwords you have stored inside. Data is stored locally.
Get it from www.mypadlock.com
Zero Footprint Crypt
Equally suited to both beginners and experts, Zero Footprint Crypt works just like a file explorer (with the same tree-style/hierarchy structure). After encryption, you can also use it to securely wipe the original file from the drive.
Get it from www.goo.gl/k4oE4 Available across multiple platforms KeePass
Perhaps the most popular cross-platform password safe, KeePass is easy to use, totally free (open source) and uses the most secure encryption algorithms around.
www.keepass.info
Lastpass
LastPass not only stores all passwords and login data, it also stays synced across browsers, giving you access to your passwords wherever you are.
www.lastpass.com Password Dragon Written using Java, Password Dragon is a password manager that works on Linux and can even be stored on and launched from a USB flash drive.
www.passworddragon.com
TrueCrypt
TrueCrypt creates a virtual encrypted disk on the machine — you can add, copy, paste files into the drive and it encrypts onthe-fly. It can also be used to encrypt external drives.
www.truecrypt.org
Apps for Android
File Locker
File Locker comes with its own file browser. You can batch select and encrypt/decrypt files irrespective of size. It also allows you to open documents from within the app and notifies you if a file is left unlocked by mistake. The interface can be configured to either display all files, only locked files or only unlocked files.
Pocket
Pocket allows you to save login information for websites, bank accounts and so on under various categories. The application requires a master password to view the data stored inside and allows you to copy text while keeping it masked. This way no one can read your login credentials even if the app is left running.
Apps for iOS
Enlume
With Enlume Password Manager, you can store your passwords and other information in a categorised way. If you categorise the information you store, it also becomes easy to search. The data is then protected by a master password—if the password is incorrectly entered too many times, it locks down the app for 24 hours.
TheVault
The Vault is a password manager for iOS devices that keeps your login credentials secure. Apart from passwords, it can also store screenshots and photos as well. All the information is stored on the device itself and it also allows importing of data from other password storing applications as well.
Apps for BlackBerry
iLocker Lite
iLocker offers enhanced security by allowing you to lock any application with a password. It can be set to lock an application after the phone is locked, immediately and even at a scheduled time. This way, not only are all your applications protected, even the content inside the application is kept safe from prying eyes.
Password Manager
Password Manager Secret Server stores important passwords in an intuitive user interface that makes it easy to organise and access. You can create a favorite list of passwords or securely share a password with any one you want. A nice touch is that it shows you which password was recently accessed or modified within the app.
7 hot dual-SIM phones in India
If it wasn't for India, there hardly would have been a market for dual-SIM mobile phones.
Today, the landscape is dominated less by local upstarts, and more by companies like Nokia, Samsung and Motorola who figure in your list of options.
If you're like most prepaid users in India, a dual-SIM phone makes sense as you get the best call rates across states when travelling. Here are seven affordable dual-SIM phones that we would recommend.
Motorola EX115
Motorola EX115 is another dual-SIM QWERTY phone, albeit a few months older. The smartphone has a 3 megapixel camera, video camcorder, large colour display and an expandable memory of up to 32GB with micro-SD card. Motorola EX115 is specially tailored for social messaging. The handset comes pre-loaded with Gmail, Facebook, Myspace and YouTube mobile apps. It offers talk time of up to 200 mins and standby time of up to 250 hours. The Motorola EX115 has a colourful 5.8 cm (2.3 inch) QVGA display and dimensions of 61 mm in width, 109 mm in length, and 12.35 mm in height.
Price (best buy): Rs 4,990
Spice Mi-270This is an Android 2.2 FroYo based, dual-SIM smartphone from Spice Mobile. It features a 7cm touchscreen, 2 megapixel camera, Wi-Fi, GPRS/EDGE and GPS connectivity. It's also the cheapest Android phone,
Price: Rs 5,700
The Samsung Corby II S3850
This is obviously the successor to the original Samsung Corby. This one includes a capacitive touchscreen along with a 2 megapixel camera, FM Radio and social networking integration. Connectivity options include Wi-Fi and GPRS/EDGE connectivity.
Price: Rs 5,600
Motorola EX128
Motorola EX128 is another dual-SIM touchscreen phone. The smartphone has a 3 megapixel camera, videocamcorder, large colour display and an expandable memory of up to 8GB with micro-SD card. Motorola EX128 comes pre-loaded with stereo FM, games, java apps, media player etc. It offers talk time of up to 200 mins and standby time of up to 250 hours. The Motorola EX128 has a colourful 3.2 inch WQVGA display and dimensions of 57mm in width, 107mm in length, and 12.8mm in height.
Price (best buy): Rs 5,990
Videocon V1855This is a dual-SIM phone with an 8 megapixel camera which is supported by flash, face detection and smile detection. It has no WiFi connectivity, but includes GPRS/EDGE capabilities. It comes pre-loaded with social networking and messaging clients.
Price: Rs 6,000
Samsung Ch@t 332This device has a full QWERTY four-row keypad and sports a 2.2-inch display. It also includes a 1.3 megapixel camera with video recording capabilities. This dual-SIM phone supports up to 8GB microSD card.
Price: Rs 3949
The Nokia X1-01
This is a phone especially built for music lovers and has a speaker vent at the back. It runs on Series 30 mobile OS and includes a 1.8-inch 16k color screen, dedicated music keys and supports up to 16GB microSD cards.
Price: Rs 2,200
What’s new @ Gmail, Hotmail, Yahoo Mail...
All major free email services have added several new features. Hitesh Raj Bhagat & Karan Bajaj tell you how to make the most of it.
Unlimited storage on Yahoo Mail
Yahoo Mail offers unlimited storage for users. No more worrying about how many heavy attachments have been sent to you. With Yahoo, you can send free text messages to cell phones. Simply enter the phone number or choose a contact from your list and type out the SMS. The recipient can reply to the SMS to send a message back.
It offers the option to view mail, SMS or Chats as a conversation for easy reading and reference. You can attach up to 25MB in a mail, however, Yahoo has tied up with Yousendit.com to send files up to 2GB in a mail.
Attachments are stored on Yousendit servers and can be downloaded for 30days. You also get 1GB online cloud storage with Yahoo as they have a tie up with ZumoDrive. A quick sign-up is required first time to integrate ZumoDrive with Yahoo Mail. After that, you can upload, download from within the mail window itself.
In terms of social networking, there is integrated Facebook chat as well as a tie up with Sobees. Sobees allows access to Facebook, Twitter, Linkedin and Myspace. You can view the feeds from various networks and update status on multiple networks in one go. There are a variety of layout options available as per your choice. Yahoo Mail also has a stationery feature, which allows mails to be created with various custom backgrounds to give it a funkier look. Another tie-up with Fontself allows you to send mail in various fonts. An integrated notepad allows you to save notes to yourself, and sort them into folders for later use.
Gmail-The best there is, with many new features
Gmail’s 7GB+ storage is constantly expanding. Plus, you can purchase an additional 20GB of space for only $4.99. Gmail’s built in audio/video chat is used by many – plus it can save all chat history. Numerous experimental 'labs' features are available to all users. Many useful features like ‘undo sending’, custom keyboard shortcuts and mouse gestures can easily be enabled from the labs menu. Completely integrates with Google Docs, Google Calendar, Picasa, Google+, Google Buzz.
Gmail’s activity tracker lets you track which IP address has accessed your account, to look out for suspicious activity (such as access from another country). For additional security of your account, Gmail offers free twostep authentication — with a password sent via sms. You can download any Google account data as a .zip file (for backup) or to free up used space in the ‘data liberation’ section.
Gmail’s contact manager has powerful editing features - it also automatically gets synced to any Android device (when you sign in with your Google account). Advanced email filters, mail sorting features (priority inbox, labels, stars, markers) make it easy to manage emails. You can pull email from any account, but also ‘send as’ from another account.
GMX-Gives you 50MB attachments with each mail
GMX offers unlimited storage, 50MB attachments on each email and an uncluttered interface with a preview pane. You can add widgets to the home page (daily comic strips, Facebook, Twitter, Google Maps, games and so on). These are visible as soon as you sign in.
The built in mail collector feature can pull in email from various accounts — to read all your mail within GMX itself. Before you decide to go with GMX, you can check for available usernames on the homepage itself — without going through any of the sign up process. GMX includes built in file storage — an additional 2GB of storage for any files.
It essentially works like a virtual drive in which you can create folders, share folders with others and download contents as zip files. Once you sign in, you get access to the GMX forum, where you can post your questions about GMX or read guides and get support on various features. You can open email in tabs within the same browser tab/window. This allows you to read/compose multiple emails at the same time. It integrates with Facebook to allow wall posting and sharing of photos.
Free Pop3/IMAP access is offered, so that you can access mail offline using any email program. The user labs feature lets you suggest new features and improvements in the platform. Once you’re a part of the community, you can activate experimental features for your account and give feedback. GMX claims to only use clean energy to power data centers.
Hotmail-Integrates with SkyDrive with 25GB free space
Hotmail storage expands as per your need. In theory, this is unlimited storage that keeps growing as you store more mails in your inbox. You can group mails from the same sender in a conversation view. This way if there are multiple emails being sent to and fro, it is easier to follow up and read. You can connect with Facebook, Myspace and Linkedin to view feeds on the home page of Windows Live.
However, if you have set Hotmail to go directly to your inbox, you will have to go back to ‘Home View’ to view the connected feeds. Hotmail Plus allows you to create as many different email ids as required with the same username by just adding a “+” sign and some text after that. The mails are delivered to your inbox and can be easily sorted due to the plus mail address.
So, if you want mails from a subscription site, simply register on the site using username+offers @ hotmail . com and it can be set to go to a specified folder. There is an easy way to view mail with attachments using the Quick Views menu. You can view only the mails that have photos or the mails that have office documents or the ones that have been flagged. Sweep functionality allows you to quickly move all mails from a specific sender to any folder of your choice. Simply select a mail received and use the sweep function.
Mail.com-Connects with Facebook for updates, photo sharing
Mail.com offers multiple domain names - you can choose from mail. com, email. com, doctor. com, techie. com and many more for your email ID. You can view emails in tabs, which allows you to read or compose multiple emails at a time. Mail.com offers unlimited storage and 50MB attachment size. Create upto 10 alias email addresses within Mail.com — email for each alias will be delivered directly to your inbox.
A handy organiser is included, accessed from the menu on top — you can add tasks, events, send email invitations, move tasks around by dragging and dropping. Personalise with various themes, change orientation of preview windows for easy reading. All the usual features like custom signatures, a vacation auto responder and custom email filters are easily accessible. You can enable a few experimental features like audio alerts for new mail and feedback mode, to help improve the service.
Mail.com offers easy online instructions to configure email with various email clients. There is complete Facebook integration — you can read/write on walls or share photos to Facebook. You only need to sign in once and allow Mail.com access to your Facebook account. Free and direct customer service is available in case you get stuck with any of the features.
Thursday, July 14, 2011
The Golden words are not Repeated
Love your job but don't love your Company,
Because you may not know when your company stops loving you.
- Dr. ABDUL KALAM
What is the Secret of SUCCESS? "RIGHT DECISIONS"
How do you make Right Decisions? "EXPERIENCE"
How do you get Experience? "WRONG DECISIONS!"
- Dr. ABDUL KALAM
Without your involvement you can't succeed.
With your involvement you can't fail.
- Dr. ABDUL KALAM
You are not responsible for what people think about you.
But you are responsible for what you give them to think about you.
- STANLEY FERRARD
A man is lucky if he is the first love of a Woman.
A woman is lucky if she is the last love of a man.
- CHARLES DICKENS
Write your Sad times in Sand, Write your Good times in Stone.
- GEORGE BERNARD SHAW
Behind every successful man, there is an untold pain in his heart.
- BILL JACOBS
It's better to lose your Ego to the one you Love,
than to lose the one you LOVE because of EGO!
- JOHN KEATS
Don't make promise when you are in JOY.
Don't reply when you are SAD.
Don't take decisions when you are ANGRYЕЕ.
Think twice, Act wise.
Wednesday, July 13, 2011
Customer complaint - good one !!!
Customer complaint : - Good one!!!
Caller : - Hi, our printer is not working.
Customer Service : - What is wrong with it?
Caller : - Mouse is jammed...
Customer Service : - Mouse? Printers don't have a mouse you fool..!
Caller : - Mmmmm? Oh really? I will send a picture.
Scroll down?
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
Moral : - Customer is always right listen him thoroughly and believe what he is saying.
The Famous Failed People - LUCK REALLY MATTERS
LUCK REALLY MATTERS
![bill-gates-impersonator[1] bill-gates-impersonator[1]](http://lh3.ggpht.com/-PBj2gUaxcKY/Th3aCaDk67I/AAAAAAAAA0c/fJ3M7E__SIw/bill-gates-impersonator%25255B1%25255D%25255B15%25255D.jpg?imgmax=800)
Bill Gates: Gates didn't seem like a shoe-in for success after dropping out of Harvard and starting a failed first business with Microsoft co-founder Paul Allen called Traf-O-Data. While this early idea didn't work, Gates' later work did, creating the global empire that is Microsoft.
![eyerman-j-r-walt-disney-of-walt-disney-studios-posing-with-some-famous-cartoon-characters[1] eyerman-j-r-walt-disney-of-walt-disney-studios-posing-with-some-famous-cartoon-characters[1]](http://lh3.ggpht.com/-S5YxdJ3NVAc/Th3aDPcFChI/AAAAAAAAA0g/BOonlIY3V9c/eyerman-j-r-walt-disney-of-walt-disney-studios-posing-with-some-famous-cartoon-characters%25255B1%25255D%25255B11%25255D.jpg?imgmax=800) Walt Disney: Today Disney rakes in billions from merchandise, movies and theme parks around the world, but Walt Disney himself had a bit of a rough start. He was fired by a newspaper editor because, "he lacked imagination and had no good ideas." After that, Disney started a number of businesses that didn't last too long and ended with bankruptcy and failure. He kept plugging along, however, and eventually found a recipe for success that worked.
Walt Disney: Today Disney rakes in billions from merchandise, movies and theme parks around the world, but Walt Disney himself had a bit of a rough start. He was fired by a newspaper editor because, "he lacked imagination and had no good ideas." After that, Disney started a number of businesses that didn't last too long and ended with bankruptcy and failure. He kept plugging along, however, and eventually found a recipe for success that worked.
![albert-einstein-1[1] albert-einstein-1[1]](http://lh3.ggpht.com/-L1EAYqtvewo/Th3aD6LS2tI/AAAAAAAAA0k/Pp_vj6XDMNs/albert-einstein-1%25255B1%25255D%25255B7%25255D.jpg?imgmax=800)
Albert Einstein: Most of us take Einstein's name as synonymous with genius, but he didn't always show such promise. Einstein did not speak until he was four and did not read until he was seven, causing his teachers and parents to think he was mentally handicapped, slow and anti-social. Eventually, he was expelled from school and was refused admittance to the Zurich Polytechnic School. It might have taken him a bit longer, but most people would agree that he caught on pretty well in the end, winning the Nobel Prize and changing the face of modern physics.
![darwin[1] darwin[1]](http://lh6.ggpht.com/-flrMM5_FjJ8/Th3aEkAOW_I/AAAAAAAAA0o/U0m3CHNmrVE/darwin%25255B1%25255D%25255B7%25255D.jpg?imgmax=800)
Charles Darwin: In his early years, Darwin gave up on having a medical career and was often chastised by his father for being lazy and too dreamy. Darwin himself wrote, "I was considered by all my masters and my father, a very ordinary boy, rather below the common standard of intellect." Perhaps they judged too soon, as Darwin today is well-known for his scientific studies.
![churchilldm0302_468x542[1] churchilldm0302_468x542[1]](http://lh4.ggpht.com/-Ij7xiWr0t2g/Th3aFUOlcBI/AAAAAAAAA0s/DrN9KVO_6-Y/churchilldm0302_468x542%25255B1%25255D%25255B10%25255D.jpg?imgmax=800)
Winston Churchill: This Nobel Prize-winning, twice-elected Prime Minster of the United Kingdom wasn't always as well regarded as he is today. Churchill struggled in school and failed the sixth grade. After school he faced many years of political failures, as he was defeated in every election for public office until he finally became the Prime Minister at the ripe old age of 62.
![2AbeLincoln1[1] 2AbeLincoln1[1]](http://lh6.ggpht.com/-cStRpipNsIE/Th3aGfnz2zI/AAAAAAAAA0w/oYTbJJh6v54/2AbeLincoln1%25255B1%25255D%25255B6%25255D.jpg?imgmax=800) Abraham Lincoln: While today he is remembered as one of the greatest leaders of the nation, Lincoln's life wasn't so easy. In his youth he went to war a captain and returned a private (if you're not familiar with military ranks, just know that private is as low as it goes.) Lincoln didn't stop failing there, however. He started numerous failed business and was defeated in numerous elections he made for public office.
Abraham Lincoln: While today he is remembered as one of the greatest leaders of the nation, Lincoln's life wasn't so easy. In his youth he went to war a captain and returned a private (if you're not familiar with military ranks, just know that private is as low as it goes.) Lincoln didn't stop failing there, however. He started numerous failed business and was defeated in numerous elections he made for public office.
![The-Oprah-Winfrey-Show-s-Final-Date[1] The-Oprah-Winfrey-Show-s-Final-Date[1]](http://lh4.ggpht.com/-q4yYi7Tvkeg/Th3aHqagRTI/AAAAAAAAA00/N3-5ue7Vm_E/The-Oprah-Winfrey-Show-s-Final-Date%25255B1%25255D%25255B6%25255D.jpg?imgmax=800) Oprah Winfrey: Most people know Oprah as one of the most iconic faces on TV as well as one of the richest and most successful women in the world. Oprah faced a hard road to get to that position, however, enduring a rough and often abusive childhood as well as numerous career setbacks including being fired from her job as a television reporter because she was "unfit for tv."
Oprah Winfrey: Most people know Oprah as one of the most iconic faces on TV as well as one of the richest and most successful women in the world. Oprah faced a hard road to get to that position, however, enduring a rough and often abusive childhood as well as numerous career setbacks including being fired from her job as a television reporter because she was "unfit for tv."
![Charlie-Chaplin_1[1] Charlie-Chaplin_1[1]](http://lh3.ggpht.com/-HCIq3OK5siQ/Th3aIKwdPfI/AAAAAAAAA1I/GNeoKPGkuww/Charlie-Chaplin_1%25255B1%25255D%25255B14%25255D.jpg?imgmax=800) Charlie Chaplin: It's hard to imagine film without the iconic Charlie Chaplin, but his act was initially rejected by Hollywood studio chiefs because they felt it was a little too nonsensical to ever sell.
Charlie Chaplin: It's hard to imagine film without the iconic Charlie Chaplin, but his act was initially rejected by Hollywood studio chiefs because they felt it was a little too nonsensical to ever sell.
![writer-JK-Rowling--001[1] writer-JK-Rowling--001[1]](http://lh3.ggpht.com/-K00VteQ_TYQ/Th3aLXBAokI/AAAAAAAAA1s/YsSzFdIXfPs/writer-JK-Rowling--001%25255B1%25255D%25255B7%25255D.jpg?imgmax=800) J. K. Rowling: Rowling may be rolling in a lot of Harry Potter dough today, but before she published the series of novels she was nearly penniless, severely depressed, divorced, trying to raise a child on her own while attending school and writing a novel. Rowling went from depending on welfare to survive to being one of the richest women in the world in a span of only five years through her hard work and determination.
J. K. Rowling: Rowling may be rolling in a lot of Harry Potter dough today, but before she published the series of novels she was nearly penniless, severely depressed, divorced, trying to raise a child on her own while attending school and writing a novel. Rowling went from depending on welfare to survive to being one of the richest women in the world in a span of only five years through her hard work and determination.
How to remove new folder.exe virus from pendrive
If you are using pen drive for data transfer at school, college or at your office you must have come across this virus. This virus creates an exe file in your USB drive with the name New Folder.exe. Here are some symptoms of this virus.
- Task manager is disabled.
- Registry Editor is disabled.
- Folder options not working.
- Taking too much time for accessing pen drive.
- Uses half of your computers processing power.
You can easily remove this virus from your computer by using Smart Virus Remover tool. It is a small 550 Kb file. Just download the file from the link given at the end of this article. Run this downloaded exe by double clicking on it. Then click on “Delete Autorun.inf file”.
After that click on” Remove virus from USB”. The virus will be removed from your pen drive. To restore your task manager, registry editor and other things which were disabled by virus – click on “Restore Default Windows Settings”.
Monday, April 25, 2011
How to clean up the junk on your PC
MUNICH: It's a familiar problem for anyone with an older computer: a PC may run lightning-fast and smooth when it's new, but over time it starts coughing up unusual error messages and unidentifiable icons appear on the taskbar.
If the computer also starts getting slower at the same time as well, then it's time for a spring cleaning.
'When any computer is used under normal circumstances, a certain volume of garbage data is automatically produced,' says Harald Goerl, a professor for operating systems and computer architecture at the Bundeswehr University in Munich, Germany. Goerl nevertheless sees no need for routine clean-ups. 'You only need to do this if you can really feel that the speed has been impaired,' he says.
The primary culprit for PC slowdowns is software that is installed and then removed again. That's because many programs actually leave behind digital traces after uninstallation. The most common collection spot where junk data collects is the Windows Registry file. It's a database of information about all installed applications.
Many programs 'forget' to delete their entry in the registry when being removed. That continues expanding the database, which means the computer has to search longer to find a specific entry. 'You can compare it with a telephone book,' Goerl says. 'The thicker it is, the longer it takes to browse through.'
You can get help in cleaning up those clogged registry files with free programs such as CCleaner, Wise Cleaner, and Advanced System Care. They search through the registry automatically looking for unnecessary entries, washing away the junk.
Linux and Apple users are actually no better off in this respect, Goerl says. 'Deleted programs leave traces behind in Linux and Mac OS, too. Because there's no central registry, though, cleaning up can actually be more difficult in some cases,' he says.
Programs that are not properly removed under Windows can create other problems as well. 'When some programs are being uninstalled, they also delete libraries still needed for other programs,' explains Joachim Geiler, dean of academic affairs at the IT working group at the Mittweida University of Applied Sciences in Germany.
Libraries are files with information that multiple programs need to be able to access. If they are deleted by accident, then applications may stop functioning, either partially or completely. This problem can generally be fixed by reinstalling the affected program.
Reinstalling the operating system is generally only needed in exception cases, says Goerl. 'Only in cases involving serious security problems should you have to reinstall the OS,' he says. 'If numerous files have been infected with tough-to-remove viruses, then reinstalling the operating system is probably the only remedy.'
The best recommendation for boosting speed that you suspect has been degraded as a result of application detritus: clean up your hard drive. 'At least 10 per cent of a hard drive's capacity should always be free,' says Joachim Geiler.
Otherwise files have to be split up across multiple sectors of traditional hard drives, and this results in data that is scattered in fragments throughout the hard drive, leading to slower access. The Windows defragmentation utility is needed to bring the files back to a contiguous state.
If you don't push your hard drive to its capacity all the time, then defragmentation need only be a seldom-used tool. 'Routine defragmentation used to be a common thing. Modern file systems like FAT32 create the files intelligently from the start, meaning users don't typically have to get involved,' says Geiler. The exception is for users who frequently work with especially large files, such as those used for video editing.
A clean hard drive is important beyond just the speed of the computer. It also makes work more relaxing. 'It's all about being able to find important files fast when you need them,' explains Joerg Schieb, who authored a book on keeping computers clean and running fast. For this reason he recommends routine cleanups every three months or so.
There are programs to help clean up, too. 'Lay users in particular may be better served by those programs,' Schieb says. Applications like TuneUp Utilities, Twin 7 2.0 from Data Becker, or PC Check & Tuning 2011 from Magix cost between 30 and 40 dollars and offer a number of cleanup options.
Thursday, April 14, 2011
U.S. shuts down massive cyber theft ring
(Reuters) - U.S. authorities claimed one of their biggest victories against cyber crime as they shut down a ring they said used malicious software to take control of more than 2 million PCs around the world, and may have led to theft of more than $100 million.
A computer virus, dubbed Coreflood, infected more than 2 million PCs, enslaving them into a "botnet" that grabbed banking credentials and other sensitive data its masters used to steal funds via fraudulent banking and wire transactions, the U.S. Department of Justice said on Wednesday.
The government shuttered that botnet, which had operated for a decade, by seizing hard drives used to run it after a federal court in Connecticut gave the go-ahead.
"This was big money stolen on a large scale by foreign criminals. The FBI wanted to stop it and they did an incredibly good job at it," said Alan Paller, director of research at the SAN Institute, a nonprofit group that helps fight cyber crime.
The vast majority of the infected machines were in the United States, but the criminal gang was likely overseas.
"We're pretty sure a Russian crime group was behind it," said Paller.
Paller and other security experts said it was hard to know how much money the gang stole. It could easily be tens of millions of dollars and could go above $100 million, said Dave Marcus, McAfee Labs research and communications director.
A civil complaint against 13 unnamed foreign nationals was also filed by the U.S. district attorney in Connecticut. It accused them of wire and bank fraud. The Justice Department said it had an ongoing criminal investigation.
The malicious Coreflood software was used to infect computers with keylogging software that stole user names, passwords, financial data and other information, the Justice Department said.
"The seizure of the Coreflood servers and Internet domain names is expected to prevent criminals from using Coreflood or computers infected by Coreflood for their nefarious purposes," U.S. Attorney David Fein said in a statement.
In March, law enforcement raids on servers used by a Rustock botnet were shut down after legal action against them by Microsoft Corp. Authorities severed the Rustock IP addresses, effectively disabling the botnet.
Rustock had been one of the biggest producers of spam e-mail, with some tech security experts estimating they produced half the spam that fills people's junk mail bins.
A botnet is essentially one or more servers that spread malicious software and use the software to send spam or to steal personal information or data that can be used to empty a victim's bank account.
U.S. government programmers shut down the Core flood botnet on Tuesday. They also instructed the computers enslaved in the botnet to stop sending stolen data and to shut down. A similar tactic was used in a Dutch case, but it was the first time U.S. authorities had used this method to shut down a botnet, according to court documents.
Victims of the botnet included a real estate company in Michigan that lost $115,771, a South Carolina law firm that lost $78,421 and a Tennessee defense contractor that lost $241,866, according to the complaint filed in the U.S. District Court for the District of Connecticut.
The government plans to work with Internet service providers around the country to identify other victims.
(Reporting by Diane Bartz and Jim Finkle; editing by Gary Hill and Andre Grenon)
Cyber attack hits WordPress.com, 18 million blogs compromised
 Automatic, the company that owns the Word Press.com blogging platform that powers more than 18 million blogs, announced this morning that its servers had been broken into and source code, among other things, could have been exposed.
Automatic, the company that owns the Word Press.com blogging platform that powers more than 18 million blogs, announced this morning that its servers had been broken into and source code, among other things, could have been exposed.
Word Press founder Matt Mullenweg writes 'Tough note to communicate today: Automatic had a low-level (root) break-in to several of our servers, and potentially anything on those servers could have been revealed.'
According to Mullenweg, the break-in was limited but proprietary information could have been accessed:
We have been diligently reviewing logs and records about the break-in to determine the extent of the information exposed, and re-securing avenues used to gain access. We presume our source code was exposed and copied. While much of our code is Open Source, there are sensitive bits of our and our partners' code. Beyond that, however, it appears information disclosed was limited.
Update: According to Automatic, this break-in 'affects most of Automatic's services Root level access potentially allows access to everything on the servers."
Tech Crunch's Alexia Tsosis argues that Mullenweg is downplaying the severity of the incident, pointing out that "Word Press.com VIP customers are all on 'code red' and in the process of changing all the passwords/API keys they've left in the source code." Tech Crunch, among other big blogs, is a WordPress VIP customer.
"While Automatic is down playing the leak, site source code includes API keys and Twitter and Face book passwords," writes Tsosis.
Mullenweg says that the investigation is ongoing and that they have "taken comprehensive steps to prevent an incident like this from occurring again."
Mullenweg also suggests that users should use strong passwords, different passwords for each site and, "If you have used the same password on different sites, switch it to something more secure." In other words - change your passwords, folks.
Tuesday, April 5, 2011
Thursday, March 24, 2011
Intel launches second generation processor - Intel Insider
Intel today launched a second generation processor called Intel Insider, a feature that will help people download and view movies in High Definition (HD) on their laptops and PCs.
The PCs and Laptops with the Intel Insider processor would be available in the country from next month onwards, Intel's Managing Director, South Asia, R Shivakumar told PTI here.
'The launch of Intel Insider in India is absolutely befitting considering it is the home of one of the largest film industries in the world -- Bollywood. With Intel Insider, people can watch their favourite movies in HD at their homes on the day of release itself,' Shivakumar said.
In a bid to boost its sales, Intel has tied-up with Hungama.com, which will act as a platform for download and streaming of famous Bollywood and international movies, including blockbusters from Yash Raj Films , Paramount Pictures , T-Series and Reliance Home Video .
The introduction of Intel Insider is a significant breakthrough in the entertainment space where consumers can unlock an ever increasing and expanding world of high- definition content on their PCs, he added.
The technology also offers a 'proactive queue' capability that will help consumers pre-download films ahead of the release date, and give them the ability to purchase those films, securely, even if they are not connected to the Internet.
This will allow consumers to start watching their movies immediately on the release date without waiting to download during peak traffic times.
Nokia job cuts might begin from April end
The world's leading mobile phone maker Nokia said Wednesday negotiations with unions over upcoming job cuts would begin at the end of April.
'We don't have an exact starting date, but we are planning to begin talks at the end of April, and then we will of course talk about the numbers,' company spokesman Tomi Kuuppelomaeki told AFP.
Nokia has not yet said how many of its 16,000 developers worldwide it will let go as part of a new corporate strategy to phase out development of its smartphone platform Symbian.
On February 11, chief executive Stephen Elop announced the company would begin adopting Microsoft's Smartphone platform instead, resulting in 'substantial' job losses.
The move was a dramatic strategy shift aimed at streamlining a company that has so far been steadily losing ground on the Smartphone market to Apple's iPhone, RIM's Blackberry, and phones running Google's Android platform.
The announcement sent shock waves through Finland, where most of the company's Symbian development is done, and where around 20,000 people work for Nokia.
Some industry analysts have speculated that up to 6,000 jobs could be at risk, with hundreds or thousands more lost among subcontractors.
Wednesday, March 23, 2011
9 Things you can do with Wi-Fi
Wi-Fi can be used for a lot more than just connecting to your computer or phone to the internet. The technology can come handy for a variety of other tasks.
Here are nine little-known uses of Wi-Fi.
Make DTH signal go the distance
Monsoon Multimedia's Vulkano is a device that connects to (and controls) your existing DTH set top box (STB).
It has to be set up so that the STB outputs to the Vulkano, while the Vulkano is connected via HDMI to the TV.
You can watch TV normally, but Vulkano also lets you stream your existing TV, which you've already paid for, to any internet-connected PC, Android phone or iPad/iPhone/iPod Touch.
Whether you're within your Wi-Fi connected home, or anywhere in the world, you can connect to the Vulkano box, switch on the STB and watch or record live TV.
If you have a recorder like TataSky+, the Vulkano box can also be used to schedule a recording on it.
At $280, this is a cool new way to make your TV channels go the distance.
Control DSLR over Wi-Fi with your iPhone
If you have an iPhone or iPod Touch, an app called DSLR Camera Remote by OnOne Software ($19.99 for the pro version, $1.99 for the lite) can work as a remote viewfiner and shutter release for one of the compatible Nikon or Canon DSLRs.
Connect the DSLR to a PC using USB, download and install the client software and then the app on the iPhone/iPod.
As long as both the iPhone and the PC are on the same wireless network, you'll be able to see what the DSLR sees, even in another room.
Apart from actually taking the photograph, you can also control the exposure and various other settings remotely.
Turn webcams into surveillance cameras
An app called iCam ($4.99) for the iPhone, iPad or iPod Touch can be used to remotely monitor your home when you are away.
You need to install the free iCamSource software (available for Windows & MAC) on each laptop or PC that you want to use, and then configure it to the iCam software in a simple , two-step process.
You can configure up to 12 different webcams with each iPhone, and view the feeds from four of them simultaneously. Like a high-end surveillance system, iCam also offers push notifications.
The app continuously monitors the camera feeds for movement. If movement is detected, a message will pop up informing you of the same.
Share Net connection using Wi-Fi
Free program called Connectify turns your Windows 7 machine into a Wi-Fi hotspot.
Download Connectify from connectify.me and set it up by giving your Wi-Fi network a name and password, just as you would with a regular Wi-Fi router.
So whether your laptop is connected via Ethernet or to a USB broadband modem, you can share internet with other nearby laptops or devices like Wi-Fi enabled phones, iPods and tablets.
Similar functionality can be found on smartphones like the Samsung Galaxy S and HTC HD2; both have built in software that lets you share your GPRS connection with other Wi-Fi devices in the vicinity.
Transfer photos from digicam to PC
Imagine a memory card for your digital camera that never ran out of space. That's what the Eye-Fi wireless SD can do for you.
The card packs in regular flash memory and a Wi-Fi adapter into a standard SD card that can fit many digital cameras.
When you first get it, you need to configure the card to your Wi-Fi network by connecting it to a PC.
You can also configure it with Flickr, Picasa, Evernote, YouTube, Snapfish, Photobucket and many more.
When you get within range of your configured Wi-Fi network, photos and videos stored on the card will automatically get transferred to your computer or connected site.
The 4GB Eye-Fi SD card is available for 3,800 (including customs & delivery) from eBay India's Global Easy Buy program.
Note: Although Eye-Fi is supported by over 1000 camera models, before buying, do check the compatibility list on the company website.
Send photos to digital photo frame
The iGala Wi-Fi photo frame looks just any other 8-inch photo frame. But it's actually pretty advanced.
Based on Linux, the touchscreen can be used to configure it to your Wi-Fi network.
Sign in to your Flickr account on it to instantly have it display photos from your stream.
You could also use it just like any other photo frame, by displaying images from the 1GB built in memory or external SD/USB devices.
Available from Thinkgeek.com for $240 (They ship to India; customs and shipping charges extra).
Make your own portable Wi-Fi hotspot
You may not always have an available Wi-Fi connection to get your fix. However , with the help of a handy new device, you can create your own Wi-Fi hotspot wherever you go.
The Tata Photon+ Wi-Fi is a small, battery-powered device that connects to Tata Photon's broadband network (just like the USB device) and instantly creates a portable Wi-Fi hotspot that can be used by up to five devices at a time.
It also has a single Ethernet port to connect to a desktop or laptop without Wi-Fi .
Buy the device for 6,499 and choose from a number of different plans starting at 500 per month.
Modern warfare with the Parrot AR.Drone
Designed solely for the Apple iOS platform, the AR.Drone is a toy quadricopter that you can control via Wi-Fi from your iPhone, iPad or iPod Touch.
The Drone broadcasts its own Wi-Fi network and connects to your iPhone/iPod once you download the free app.
Each pairing between an AR.Drone and iOS device is unique, so you can even have multiple Drones in the same area.
Meanwhile, two cameras built into the drone relay a live video feed directly to your iPhone/iPod so that you can send it along on reconnaissance missions (just don’t stray too far away).
Multiple AR.Drones can take on each other in a dogfight or a race around obstacles if that takes your fancy.
For indoor use, the supplied hull shield needs to be out on that surrounds the rotors and protects them from any impact against the wall or other Drones.
The hull can be removed for outdoor use.
The Parrot AR Drone is available from international reseller shopyourworld.com for 21,000 (including customs and all shipping charges)
Monitor entire house with Rovio
Rovio is a toy, but a pretty advanced one at that. The battery-powered, camera-toting and Wi-Fi enabled Rovio will wait patiently at home for your command. Connect to it from a remote location, and you'll see what Rovio sees.
You can also move Rovio around and use it to communicate with other people thanks to the built in speaker and mic.
Teach Rovio your home's layout by setting waypoints and Rovio can navigate to those preset locations all by itself.
And Once Rovio's battery is depleted, it can automatically back itself into the charging dock at home.
Available from http://jmdcomputerindia.com for $199 (They ship to India; customs and shipping charges extra).
Acer launches Android-based Liquid Metal
Acer has expanded its Smartphone portfolio in the country with the addition of Acer Liquid Metal. Acer Liquid Metal is based on Android 2.2 (Froyo) operating system and runs on 800MHz Qualcomm Snapdragon Core processor.
Measuring 115 X 63 X 13.5mm inches, the Smartphone has a curved 3.6" display with a TFT capacitive touch screen. The Smartphone has a stainless steel battery cover, which is solid and resistant.
The Liquid Metal supports HSDPA for on-the-go Internet access at speeds up to 14.4Mbps as well as Wi-Fi allowing data transfer 10 times faster than previous devices. The LED signal on the upper part of the telephone notifies the user of missed calls, the need to charge the battery, and new incoming messages clearly.
Acer Liquid Metal's 1500 mAh battery coupled with intelligent power management means you have up to 8 hours talk time and 550 hours in standby mode. Acer Liquid Metal comes with 3 popular keyboard layouts including Clever XT9 predictive text support to save users typing unnecessarily.
Liquid Metal is built in with a pinch to zoom feature, 5-megapixel camera with digital zoom, LED flash with a maximum resolution of 480 x 800 pixels. The camera offers 720p HD video recording as well as autofocus and smile recognition.
Key specs:
* Powered 800MHz Qualcomm Snapdragon Core Processor
* Android 2.2 Froyo OS (5X faster than the earlier versions)
* Display : 9.1 cm (3.6-inch) TFT capacitive touch screen, 16M colors, 480 x 800 pixels resolution
* Fastest Connectivity Suite : HSPA 14.4 MBPS , 3G (3G + WiFI), GPS, Mini USB
* Record video in HD at 720p (30fps)
* Dolby Surround technology , EQ profiles and Dynamic Bass Boost Push Mail
* 3 Predictive Dialers (3 KB with XT 9)
* Superior Battery Life up to 8 hrs of talk time (1500 MAH Battery)
* Top LED Indicator
* Accelerometer sensor for auto-rotate
* Wireless LAN Wi-Fi 802.11 b/g/n, UPnP
* Bluetooth v3.0 with A2DP
* Camera: 5 mega-pixel,auto-focus, LED flash ,Geo-tagging, face and smile detection, image stabilization
* Unique Acer Interface
* Pinch to Zoom option
* 8GB Micro SD Card (up to 32GB)
Available in silver, brown and tiffany Blue colors, Acer Liquid Metal is priced at Rs. 20500.
Monday, March 21, 2011
CISCO - LINKSYS E-1000
GO WIRELESS AND EASILY PUT THE SPEED AND POWER OF WIRELESS-N TECHNOLOGY IN YOUR HOME…..
PRESENTING LINKSYS E-1000 WIRELESS N ROUTER……..
BEST FOR : -
STANDARD, QUICK TO INSTALL, WIRELESS – N CONNECTIVITY FOR SURFING THE WEB, SENDING EMAIL AND FILE SHARING….
BENEFITS : -
Ø WIRELESSLY SURF THE WEB AND SEND E MAIL.
Ø SHARE FILES AND PRINTERS
Ø QUICK SET UP
PASSWORD PROTECTED GUEST ACCESS, PARENTAL CONTROLS, ADVANCED SETTING
HOW WE DO IT :-
Ø WIRELESS N TECHNOLOGY WITH 2 INTERNAL ANTENNAS
Ø 2.4 GHz BAND OPERATION
Ø CISCO CONNECT SOFTWARE
Ø ADVANCED SECURITY AND FIREWALL PROTECTION
Specifications
Ø Standards : 802.11n, 802.11g, 802.11b, 802.3, 802.3u
Ø Ports : Power, Internet, and Ethernet (1-4)
Ø Buttons : Reset, Wi-Fi Protected Setup
Ø LEDs : Ethernet (1-4), Wi-Fi Protected Setup, Wireless, Internet, Power
Ø Cabling Type : CAT 5e
Ø RF Pwr (EIRP) in dBm : 17.5 dBm
Ø Antenna Gain in dBi : 1.5 dBi
Ø UPnP able/cert : Able
Ø Security Features : WEP, WPA, WPA2
Ø Security Key Bits : Up to 128-Bit Encryption
Environmental
Ø Dimensions : 7.95" x 1.34" x 6.3" (202 x 34 x 160 mm)
Ø Weight : 9.81 oz (280 g)
Ø Power : 12V, 0.5A
Ø Certification : FCC, CE, IC-03, Wi-Fi, Windows 7
Ø Operating Temperature : 32 to 104°F (0 to 40°C)
Ø Storage Temperature : -4 to 140°F (-20 to 60°C)
Ø Operating Humidity : 10 to 85% Noncondensing
Ø Storage Humidity : 5 to 90% Noncondensing
Please call for any support or inquiry….
Sunday, March 13, 2011
ViewSonic ViewPad 10 tablet review
The first dual-boot tablet is surely worth a look, but needs a price cut.
There are a lot of tablets that have been launched in India within the past few months and more are on the verge of being launched. Most tablet manufacturers have chosen to go with Android as the operating system, whereas few others have chosen Windows 7. However, ViewSonic comes with a tablet that dual boots both operating system, that almost provides the user best of both sides.
Looks & Ergonomics
The ViewPad 10 is not the slimmest or the sexiest tablet out there, but its got a vibrant 10.1” display. There are three touch sensitive buttons on the matte finish bezel that extends below the glossy bezel and perform different functions under the two OS. There is a 1.3MP front camera present as well. The tablet has two full size USB2.0 port, mini VGA port, microSD card slot and 3.5mm audio jack and microphone on the side. The back has a brushed metal finish with the ViewSonic logo printed in the centre with speakers and heat vent at corners.
The tablet weighs just under 1kg and was easy to use with two hands. Using the tablet in vertical as well as horizontal position did not pose any problem. The brushed metal back and the matte finish bezel provide excellent grip.
Display
The tablet has a 10.1” capacitive touchscreen with a resolution of 1024 x 600 pixels. We loved the touch response on the tablet and multi-touch worked superbly across windows and android. Of course, like every other tablet out there, the large display is a fingerprint magnet and requires cleaning every now and then.
Hardware & Software
The ViewPad 10 is powered by an Intel Atom processor running at 1.66GHz with 1GB of DDR 3 RAM along with 16GB SSD storage. The SSD provides quick boot up and thought the hardware is more than enough for Android, 1GB RAM makes the overall windows experience slightly sluggish. It comes with WiFi b/g/n, Bluetooth, 3G and assisted GPS. The tablet also has a G-sensor, E-compass sensor and an ambient light sensor.
The tablet comes loaded with Windows 7 Home premium and Android OS v1.6 as operating systems, which can be selected, on start-up. We loved the fact that Windows on the tablet performed the same way on a laptop. In fact, when we tried connecting to the Internet using a Reliance Netconnect USB modem, it worked flawlessly. We installed various windows application and other than the slight sluggishness due to low RAM we faced no issues.
It comes with Android is v1.6 and ViewSonic has no plans to upgrade it on the tablet. The performance on Android is fantastic, though due to the older version the number of apps is limited across categories.
Multimedia
Thanks to Windows 7 and the full size USB 2.0 port, the ViewPad tablet provides for the easiest access to multimedia. Like a standard desktop, various codecs and multimedia player could be loaded allowing the user to play any format of video as well as audio. Watching videos on the tablet was superb due to the large sized display. The sound output from the tablet is not too loud, but is higher than that for personal listening. The sound output in the earphones is great though with excellent clarity.
User Interface
ViewSonic has not done any modification across either of the interface than the standard wallpaper change to Viewsonic’s logo. Windows 7 interface is like a standard laptop, instead of physical mouse and keyboard; the user gets an onscreen keyboard and the multi-touch display to work with. In Android, it’s the same basic android interface that was in phones around a year back.
Conclusion
Although, the tablet has excellent hardware with a great touch-screen display, it’s the dual-boot operating system that is the major advantage over competitors here. However, we barely used the Android operating system over windows as it provided more options. The battery backup of the device lasted us just over a day, which is impressive considering we constantly worked on it and it was connected through WiFi constantly.
The ViewPad 10 is priced at Rs 38,000, which is too steep for an average consumer who now has options in terms of the MSI Windpad at 35,000 and the Apple iPad starting from Rs 28,000 in the same screen size.
Specifications
10.1" LCD screen with Capacitive multi-touch screen
1024x600 with LED backlight
220 cd/m2 Brightness
700:1 Contrast Ratio
Intel Pine Trail N455 1.66GHz processor
DDR3 1GB SDRAM 667MHz
16GB SSD SATA
Wi-Fi (802.11 b/g/n), Bluetooth 2.1 (optional 3G module) + EDR, 3G and assisted GPS
Windows 7 Home Premium
Android 1.6
0.875 kg
1.3 megapixel camera (front)
G-Sensor, E-Compass sensor and ambient light sensor
Ports-3.5mm audio jack for stereo headset, 2 USB 2.0 ports, mini VGA port, Micro SD card slot
Start your day with the LD2 Daily Bytes newsletter. It's the best gadget advisor in the country.
HP Dreamscreen Review
A fancy desktop with lots of eye candy, but very limited use
Touchscreen tablets are expected to be the top selling gadget this year. With around 100 tablets announced at CES, touchscreen devices seem to be the direction to go. Looking at all the hype, HP has tried to go a step ahead and instead of providing a portable tablet; they incorporated touch-screen into their new desktop offering called the DreamScreen.
The DreamScreen is pure eye candy in terms of looks. This All-in-one desktop has a large 18.5” display with 1366 x 768 resolution. The display has a clear plastic bezel around the display frame that adds to the looks of the system. There is a large indicator right at the front bottom that looks like a power button, but works only as a power indicator. Other controls are placed on the right hand side. All the connectivity ports for USB and card reader, headphones are placed neatly on the left hand side with additional ports at the back. There is also a slot load DVD drive on the right hand side just above the control buttons. All in all, the Dreamscreen looks very good and can easily add to the décor of a room. The only issue is that it takes a wire with an adapter for power that is clearly visible behind the monitor.
The HP Dreamscreen is powered by an Intel processor and comes with a 250GB hard-drive. There is very little information about the hardware that has been shared by HP. It comes with a mouse and keyboard as well even though the onscreen keyboard of the PC is very responsive and easy to use. It has inbuilt WiFi for connectivity and also comes with an Ethernet port at the back.
The desktop runs on a Linux based operating system, which has been heavily customized. The interface has been tweaked to be touch-interface friendly. The good thing is that HP has provided large icons to use on the desktop for various activities. You can either log in as the administrator or as an student. The student account has limited privileges in terms of installing and purchasing content. HP has tied up with various vendors to provide content on their machine across categories such as News, music, videos etc. Some content is paid, while other is free. Video streaming is free from various channels, whereas to use application for astrology, you need to subscribed etc. The User interface overall is very easy to use and quick to respond.
What we didn’t like was the operating system is too limited and restricted. It will play media of very few formats, does not remember your last sites/applications and does not even remember you WiFi connection password on restart. Moreover, a user cannot install additional applications, which is a major downer.
The HP dreamscreen is priced at Rs 19,999 and is aimed at the mid-level consumer who wants to have a good looking desktop with internet and multimedia capabilities.
Start your day with the LD2 Daily Bytes newsletter. It's the best gadget advisor in the country.
Whats Hot
- Looks
- Easy to use
- price
- touchscreen
-
Whats Not
- restricted OS
- paid subscription model
- limited media support
Estimated Street Price
Rs 19,990/-
BELKIN Play Max wireless router
One of the best routers available today with just one flaw. The name ‘Play Max’ raised our expectation before we actually tested this IEEE 802.11n based router and when we did it we were not at all disappointed, in fact disappointment came from other features. 
Once out of box what you have in hand is a compact clean looking router with hidden antennas and single indicator light and WPS button in front for hassle free secure connection setup. Number of connection ports at back is where Play Max has edge when compared with other similar products; there are 5 gigabit ports (1xWAN, 4xLAN) which would be ample for any wired connection plus being gigabit would mean faster data transfer speeds. 2 USB 2.0 ports are also present at the back for connecting external USB based storage devices with FAT 16/32 and NTFS file system, USB printers are also supported by Play Max giving you ability to convert your USB based printer to network one.
Setting up this router was the simplest of jobs and a mere 3 step process with initial configuration provided in small booklet attached to box. To use most of the features of this router including using USB storage/printer you have to install router management software that would sit in task bar and add to CPU usage, which as per us is a major con of Play Max. The main issue we faced with the router was that it does not support plugging in a 3G USB modem.
To test the performance of this router which supports true dual band in 2.5 Ghz and 5 GHz band respectively, we carried out two tests. First we used Qucheck 3.0 to test throughput, we connected one machine with wire to router and other wirelessly to N based laptop (both laptop and machine were running Windows 7) and then checked throughput over TCP protocol. Play Max was able to transfer 1000 Kb payload at 64 mbps which is one of the best scores we have seen. In second test we transferred 40 MB of mixed data from machine to laptop; Play Max was able to complete this transfer in 4 seconds which is again very high when compared to other products. We also tried using the router to stream HD videos from a windows media center to an Xbox 360 over WiFi, and it worked great.
Besides performance and features there are number of bundled utilities for different purposes like torrent gene for downloading files to external storage, bit boost for traffic prioritization, music mover for wireless music play from external storage. All in all, a high performing router with not so user friendly bundled software.
Wednesday, March 9, 2011
XPRSS – easy to use feed reader for BlackBerry
XPRSS is a fast, clean and easy to use feed reader for BlackBerry smartphone users. There are very few feed readers available in the market which can come anyway near XPRSS.
XPRSS comes preloaded with variety of feed categories. You can easily add new feeds of your choice. Variety of options are available for the user to choose from. One can add feeds to the reader directly using the feed url or just by giving the main website address and it will automatically find the feed location.
The most useful feature of it is it also allows the user to import feeds using OPML. So if you are an existing google feed reader user or using some other software to manage your feeds, you can simply export your feeds and import it into XPRSS.
If you like sharing what you discover then again XPRSS comes handy. It allows you to share articles directly from the post page to almost all popular social booknarking and social media sites. So if you are a BB geek and love to stay updated all the time then XPRSS is a must have app for you.
Download XPRSS for blackberry (Freeware)
Friday, March 4, 2011
3 free softwares to turn your Webcam into video surveillance camera
There are many situations in which you require to monitor your work area or your home. Here we have few free softwares which can turn your Webcam into a surveillance camera .
1. Rise Sun:
Rise Sun is a free Windows based video security software. Which uses a webcam for motion detection. In case of any movement detection it automatically takes a snapshot and saves it on your hard disk. It can ring an alarm if any movement is detected. You can read more about this software and download it from here.
2. TeboCam:
TeboCam does the same job as Rise Sun. But it can send you emails also in case of any activity. TeboCam can generate snapshots at regular intervals and if any movement is found it can create emails and send the snapshots to you via mail or it can directly upload it on the website. To know all the features of it just download it and use it . Here is the download link. TeboCam
3. Prog’z WebCamSpy:
Prog’z WebCamSpy is not as good as the previous two softwares mentioned here. But it can be used to make your webcam a spy cam. It is a lightweight software. Does not require much resources to work. It just sits silently and takes snapshots using webcam at regular interval and saves them on your computer. It also can zoom on particular portion while recording so you can use it for monitoring specific areas. Download Prog’z WebCamSpy
If you know any other good software which can be used for the same purpose then please share it with us using comments form below.
Interesting story behind Trojan Horse
We all have heard about the viruses named Trojan Horse, Trojan Horse is a kind of virus which appears to perform it’s intended tasks, But silently steals all the information from your computer or harms your computer in a way which may be difficult to recover.
Interestingly I got to know a story about the name Trojan Horse virus, Here it goes…
In Greek Mythology they believe there was a city called, City Of Troys & there was other kingdom of Greeks. They fought for about 10 years and the war was called the Trojan War. After 10 years of fight the greeks still had nothing in their hands, it was a fruitless siege , So the greeks declared that they quit from the War.
Now the greeks built a giant horse made of wood & gave it as a trophy of victory to the citizens of Troy called TROJANS. The trojans happily took the horse inside the city. On the same night the trojans were busy celebrating their victory while 30 soldiers who were hiding inside the Giant Wooden Horse came out & opened the city gates for the Greek Army. The Greek army then destroyed the entire troy city.
Since then everything that causes the target to bring a vulnerable object in to a secured area is referred as a Trojan Horse. Hence the name Trojan Horse is given to viruses that pretend to be something else, but once they are inside the system they start messing up the entire system.
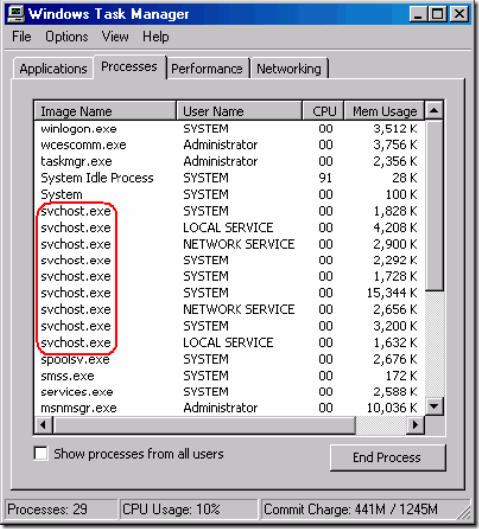
SvcHost Exe process info & virus details
What is an SVCHost.exe file? & What is it doing in your task manager?
An svchost.exe file is a windows generic host process & is there for a good reason, This files is a native integral part of the windows operating system. It basically supports various windows services running from the Dynamic Link Library (DLL) files of windows. The services that may require SVCHOST.Exe include Windows Firewall, Automatic System Updates, Windows themes , Plug and play, Fax & printer services & many more. These services ideally start automatically when the windows system starts. These files are found in all windows operating systems launched after windows 2000 NT. (i.e Windows XP, Vista & 7).
When your windows system boots, The Svchost.exe file checks the windows registries & automatically builds a list of services that needs to be loaded. Usually each SVChost.exe carries different services from windows. If you find multiple SVChost.exe files in your task manager, there is nothing to worry about, it’s absolutely normal for windows to run multiple svchost.exe simultaneously.
SVCHOST.exe Virus & Removal
It is possible for malicious software’s to modify the windows registry & make SVCHOST.exe process to load the wrong malicious .dll files. Which will endup in making your computer or network affected with viruses and malewarez.
Another common approach is those viruses files are names SCVHOST.exe did you see the difference in the filenames? SVC vs SCV??
What this file sCvhost.exe does is that it allows hackers to access all your personal information, This is a virus of tye W30/Agobot-S, You may also call this a trojan horse. Since it hides itself with a genuine process name.
How to remove Svchost.exe virus or sCvhost.exe virus:
1. Removing the Svchost virus can be a very tedious task, Though i personally managed to somehow remove the virus using advanced tactics, It is not recommended that you try and follow the same, Because a single mistake could lead to a damaged Operating system, Which would be difficult to recover.
2. So instead of giving you the steps I find it appropriate to suugest you that you should use an Anti-virus to do this for you.
3. You can grab your self a free copy of antivirus over here (Norton Internet Security).
100% CPU utilization error in SVCHOST.EXE Process & Memory Leaks:
The first solution to this problem is that you may just want to restart the computer, Most of the times this will solve your problem, Another quick solution for this problem is to start the task manager & find the process causing this problem & then right click the process name and set the priority to low.
Thursday, March 3, 2011
Interview Tips
Entering in the Room
Enter in the room with due permission of the interviewer. Shake hands firmly and wish the interviewer as per time of day. Radiate your confidence with smile. Dress conservatively. Be always on time. Be a stickler for promptness while answering the questions with aplomb. Spontaneity is the buzzword. Remember the interviewer's name.
Body Language
When the interviewer tells you to sit or gestures you to sit down then do so after thanking him. Look alert. Sit up erect. Maintain eye contact with the interviewer all the time. Speak with confidence and assurance. Interviewers like candidates who are not shaky but are enthusiastic and responsive.
Straight Answers
Answer questions openly, spontaneously without holding back and beating about the bush. Yet be direct and to the point, avoiding long, drawn-out explanations. It never pays to present answers made up of miscellaneous or incongruous ideas.
Keep it Simple and Straight
If put on the defensive (e.g. "Why do you shift jobs so frequently?" Why are you changing now?") answer as simply and succinctly as possible. Keep smiling.
No Carping
Don't dwell on carping and caviling at faults of manner of previous or present employer.
Be Courteous
Do not smoke or chew gum during interviews. It shows the disrespect towards interviewer. Do not ask direct questions about salary or other benefits at the beginning of the interview. Do not slouch in the chair, tap your feet, play with eyeglasses, pencil, or fidget nervously.
Learn about the Company
Do your homework and learn as much as you can about the company and the job requirement.
Start from the Basics
Prepare and rehearse common questions and answers. For example - What was the nature of your job? What special skills did you acquire? Were any special goals were set for you? What was your day was like on your job? What were your strengths? Weaknesses? Why are you considering leaving your present job? Why are you interested in this company and how can you contribute?
If you have it, Flaunt it
Ergo, stress your achievements. For example: Processes developed, sales records achieved, systems installed, absenteism reduced, product or production improved, etc.
Leave the Door Open
Never tell the interviewer that you are not interested in the job. Leave the door open. The first interview is not the place to turn down an offer. Do not tell about interviews you have had or plan to have.
Ask for the Job
If you are favorably impressed and know all the details of the position, then ask for the job.
Say Thanks while Concluding the Interview
While concluding the interview, thank the interviewer for the time and consideration given you. Ask when you should meet again to discuss the position further. It often takes several interviews to obtain the job offer. Ask for a business card and give yours in return.
Don’t be Anxious
There should be no room for anxiety even if you need the job desperately. (The company wants someone who is a winner and in demand.) Don't give the impression that beggars can never be choosers. Ask questions about the position -- show your serious and genuine interests in the duties and responsibilities of the position.
Besides the Interviewer is No Less Perplexed Over the Knack of Interviewing
Modern industry is highly complex and work life in general, has generated an increasing awareness of interdependency of tasks / roles and the need to understand the individual’s preferred / dominant patterns of behavior, particularly in relation to people and in groups.
Knowledge and skills assessment alone have been shown up to be inadequate in predicting success in roles / organizations. This is further aggravated by the fact that presence of knowledge / skills is no guarantee that they will be deployed as desired.
Personal Interviews as a tool for Selection and internal sourcing, while being the most popular, promises much but often suffers on many counts.
Not enough interviewers are trained in the art of interviews. They are not prepared in advance; the process is often led less by the interviewer’s ability and more by his confidence in his judgment of people. They tend to play pop psychologists.
Not enough time is invested in the process to look for evidence and consistent patterns of behavior, extrapolations, assumptions and conjectures are made about how a candidate is likely to be / behave from limited data about the candidate. Interviewer’s own world-views, biases and prejudices (personal stances) affect his judgment. Focusing on what a candidate "knows" to the near exclusion of a good probe on "what" a candidate has done, "how", and the nature of his interfaces with others and the world at large.
Standardization of interview items and sequence, rigor in established benchmarks for responses andappraisal of responses is shunned as tedious, impractical and at best insipid and monotonous. The bottom line is: Comparisons are difficult and choice making is largely subjective, the "feel good" factor dominating the decision.
It is now well established by research that an individual’s values, motives, traits and other components that constitute the core of personality have a more enduring influence on patterns of deployment of energies and behaviour. Factoring these in decision making on selection, fitness and development planning thus makes sound business sense.
Assessment tools developed by experts to profile aspects of personality provides a reliable basis for data generation about individuals and is time / cost effective! Professionals help in the absence of relevant training to interpret results of these tests is a useful step.

 9:41 PM
9:41 PM
 Sanket Barot
Sanket Barot